PRECONDITIONS
- You completed onboarding with Luware Nimbus.
- You have tenant admin rights in your tenant.
- You have a reporting user (a user with Role "Tenant Admin, User Supervisor, Team Owner or Service Owner").
- You need to know which cluster you are in (Germany, Switzerland, UK, etc.).
🔍 Note: Read more about how to grant global tenant-wide consent to an app documentation here: Microsoft Learn || Grant tenant-wide admin consent to an application.
Using Postman or other API clients
You can connect to the OData Feed via API using various clients. https://www.postman.com/ is very handy when it comes to exploring the API's methods and data.
☝ By default, an explicit login is forbidden. Your tenant admin needs to grant this type of access first.
INC Icon Legend Accordion
Show Icon Legend
| 💡 = A hint to signal learnings, improvements or useful information in context. | 🔍 = Info points out essential notes or related page in context. |
| ☝ = Notifies you about fallacies and tricky parts that help avoid problems. | 🤔 = Asks and answers common questions and troubleshooting points. |
| ❌ = Warns you of actions with irreversible / data-destructive consequence. | ✅ = Intructs you to perform a certain (prerequired) action to complete a related step. |
Register Enterprise Application "Nimbus Odata Login" in your tenant
-
We will first need to add the application ID of the “Nimbus Odata Login” app (898a7352-9216-4ca8-a485-7d8f3903f598) to your tenant via PowerShell, using the Microsoft.Graph.Applications PowerShell module. If this module isn't already installed on your local system (see the output of
Get-Module -Name Microsoft.Graph.Applications -ListAvailable), run the following command first:
Install-Module -Name Microsoft.Graph.Applications -Scope CurrentUser-
The next commands will connect to Graph and attempt to add a new service principal for the application ID.
💡 Note that these can only be executed by a user with an appropriate admin role in Azure, such as Global Administrators.
Connect-MgGraph -Scopes Application.ReadWrite.All
New-MgServicePrincipal -AppId 898a7352-9216-4ca8-a485-7d8f3903f598- Next, replace {tenant-id} in the following URL with your Azure tenant ID, open it in a browser and login with your tenant admin to accept the permissions:
https://login.microsoftonline.com/{tenant-id}/adminconsent?client_id=898a7352-9216-4ca8-a485-7d8f3903f598
- Open https://portal.azure.com/, navigate to Enterprise applications and verify that the Nimbus OData Login enterprise application is available, and has the correct permissions granted.

💡 Now users should be able to login with an OAUTH 2.0 token.
Open the postman collection
-
Download the postman collection here and open it in your postman client.
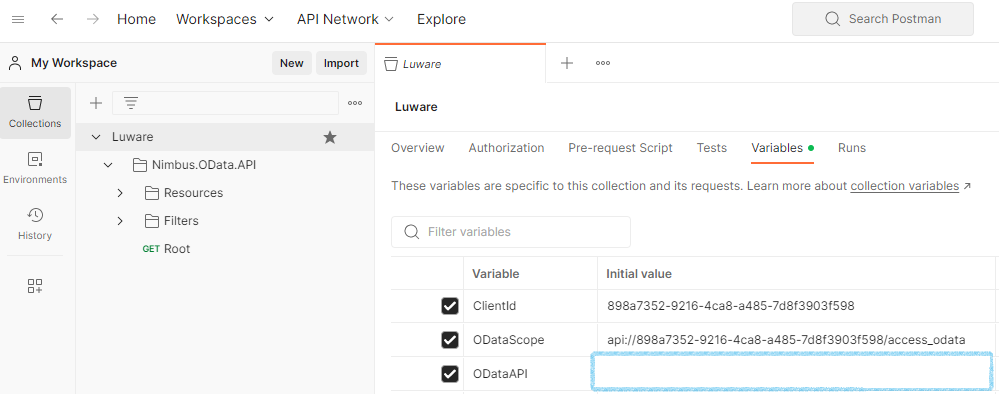
- Update the variables according to your environment:
| Variable | Purpose | Value | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ODataAPI | The URL of the OData API | Nimbus API URLs: INC Nimbus API Connector URLs
✅ Make sure to configure your web proxies to allow access to these domains or whitelist the complete *.luware.cloud domain. |
||||||||||||||||
| ODataScope | The scope of the access request | api://898a7352-9216-4ca8-a485-7d8f3903f598/access_odata |
||||||||||||||||
| ClientId | Nimbus OData application ID |
|
Verify access to the Nimbus OData application
-
Navigate down to the folder “Nimbus.OData.API” and open the Authorization tab. The authorization type should be OAuth 2.0.
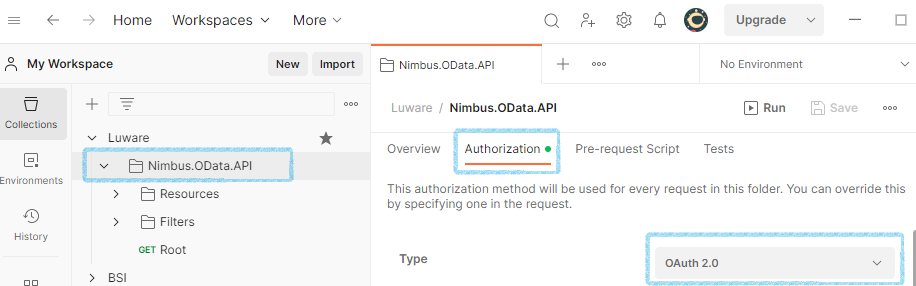
- Scroll down to “Configure New Token”. Follow the next chapters for implicit / explicit access.
Implicit Access
Configure implicit access
Send the response that opens an implicit login window. Login with your tenant admin. You should get an access token.
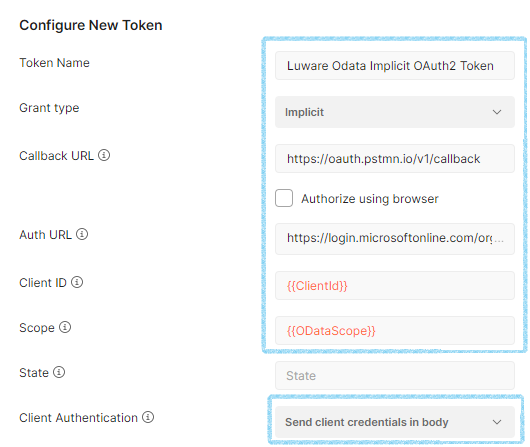
| Request GET | https:// {{ODataAPI}} /v1/odata or https://api.luware.cloud/v1/odata |
|---|---|
| Token Name | Luware OData Implicit OAuth2 Token |
| Grant Type | Implicit |
| Callback URL | https://oauth.pstmn.io/v1/callback |
| Auth URL | https://login.microsoftonline.com/organizations/oauth2/v2.0/authorize |
| Client ID | {{ClientId}} or 898a7352-9216-4ca8-a485-7d8f3903f598 |
| Scope | {{ODataScope}} or api://898a7352-9216-4ca8-a485-7d8f3903f598/access_odata |
| Client Authentication | Send client credentials in body |
Explicit Access
Configure explicit access
For explicit access using a username and password, create two additional variables for Username and Password and configure the values as below:
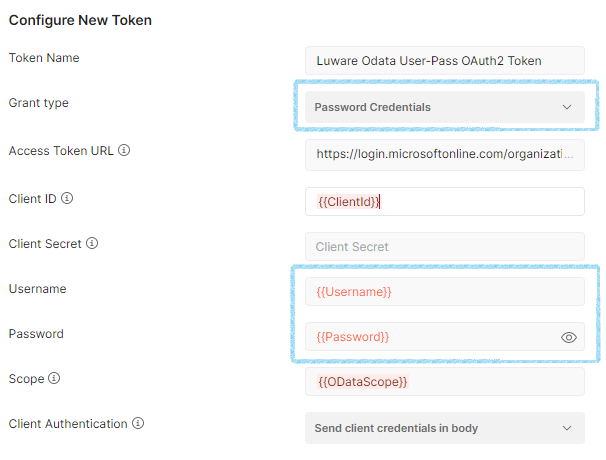
| Request GET | https:// {{ODataAPI}} /v1/odata or https://api.luware.cloud/v1/odata |
|---|---|
| Token Name | Luware OData User-Pass OAuth2 Token |
| Grant Type | Password Credentials |
| Auth URL | https://login.microsoftonline.com/organizations/oauth2/v2.0/authorize |
| Client ID | {{ClientId}} or 898a7352-9216-4ca8-a485-7d8f3903f598 |
| Username | {{Username}} |
| Password | {{Password}} |
| Scope | {{ODataScope}} or api://898a7352-9216-4ca8-a485-7d8f3903f598/access_odata |
| Client Authentication | Send client credentials in body |