This page explains the access concept of Nimbus. In the first part we explain how user rights are synched between Nimbus and MS Teams and where Nimbus acts with standalone concepts. The second part covers Roles available in Nimbus and their detailed permissions.
Teams, Users and Organization Units
Nimbus has a user roles and permissions system that grants permissions based on a Organization Units hierarchical structure. By using this concept, access to configuration entities of Nimbus can be granted on a very granular level. To understand this permission system we need to explain a few related concepts in the following.
| Concept | Details | Diagram |
|---|---|---|
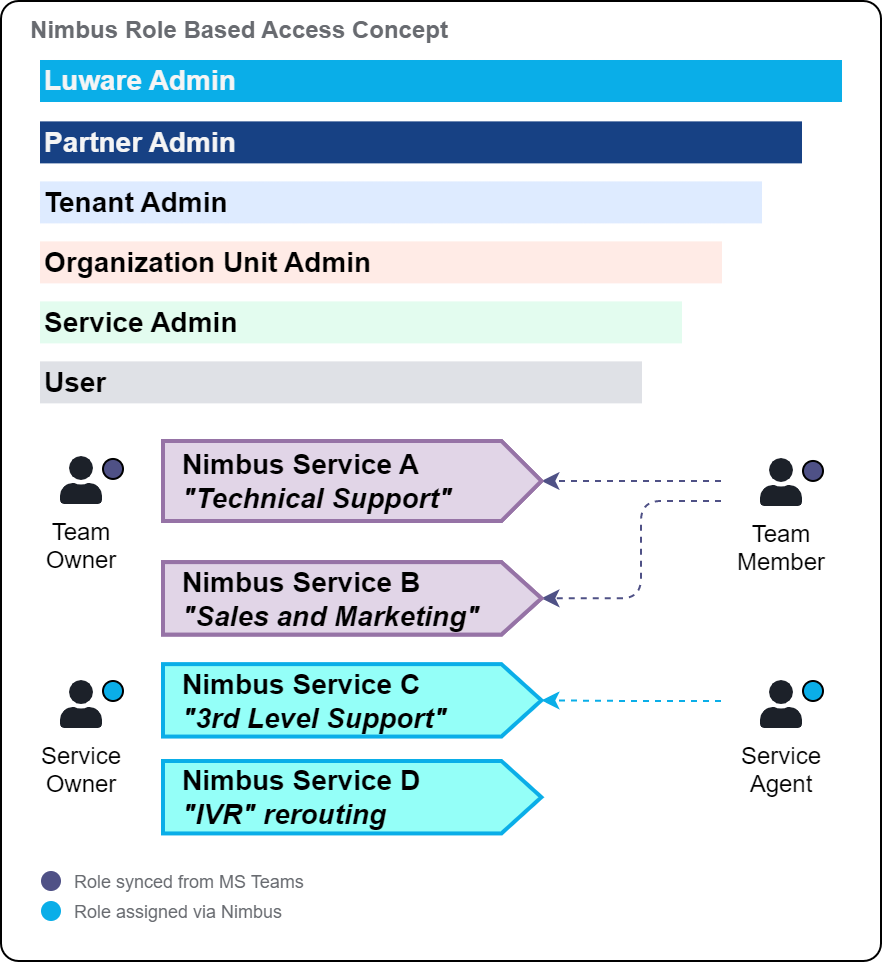
| User roles and sync between MS Teams | Nimbus syncs users from your tenant's user directory. Each user can then added in a Nimbus role, e.g. as Admin, Owner or Member/ Agent of a service. The role determines, what a user can do within Nimbus.
🔍You can find detailed permissions behind each role explained in the "Role Permission Matrix" table below.
Depending on what Nimbus Service types are being provisioned on your Tenant, Nimbus distinguishes the user role sync by their User assignment types.
🔍 More details on the assignment type and individual user roles are explained in the Role Permission Matrix chapter below. |
 |
| Access to data entities within an Organization Unit scope | As more users on your Tenant get roles assigned, it's important to distinguish where users can act this role. This is where the Organization Unit concept comes into place:
To understand Organization Units, it is important to know their relationship in the RBAC model. OU STRUCTURES AND RBACEach configurable element in Nimbus is called a data entity.
Organization Units provide a structure to all data entities, e.g. by mirroring a company's organization levels and departments.
RBAC - Role Based Access Control restricts and grants access within any Organization Unit, e.g. by assigning functions to users according to their role in the organization.
|
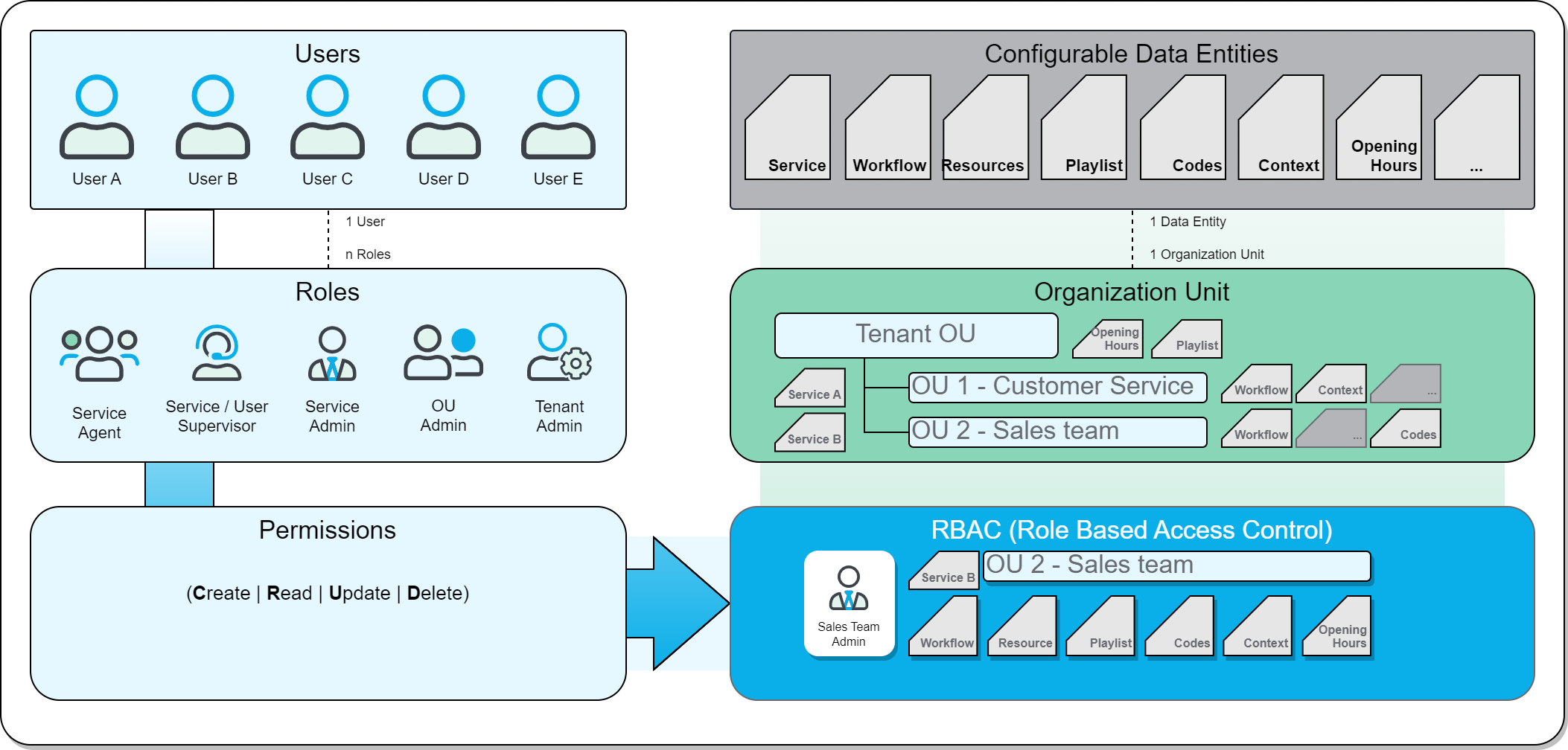 💡 Organization Units determine where a configurable data entity is placed. Each data entity must belong to exactly one Organization Unit. This includes all Nimbus users, as their OUs determines from which "point of view" they can act in their role.
💡 RBAC determines which actions (Create, Read, Update, Delete) are possible on configurable entities.
💡User roles define a set of permissions on such entities granted within one or multiple Organzation Units. |
User Role Permission Matrix
The following tabs are taken from the following pages:
User Role (RBAC) Matrix
🔎User roles in Nimbus are primarily distinguished by:
- Admin Portal - to administrate the entire Tenant settings, configure Services and Users as well as related integrations and settings.
- User Portal - to handle daily tasks in Nimbus, inspect daily Service reporting metrics and adjust corresponding settings.
- Power Automate - to handle integrations to external systems, schedule or update ongoing Nimbus tasks via Nimbus Power Automate Connector.
- Reporting - to access historical Nimbus Reporting data, either directly via OData Feed or via Nimbus Power BI Template template.
💡Good to know: Some roles automatically have access to multiple areas, while additional roles may be needed on the same user for extended access and functionality. Individual role requirements are part of the (✅ green color-signaled) preconditions chapters on respective pages of our Knowledge Base.
🔎How to read this page: Tables below list detail permissions of the Role Based Access Concept (RBAC), granting access to all Nimbus Features. All permissions are structured by the C.R.U.D.E (Create, Read, Update, Delete, Execute) principle.
Admin Portal User Permissions
Admin Roles
NOTES
Admin roles described on this page have access to the Nimbus Admin (Backend) Portal.
Show Admin URLs…
Nimbus Admin URLs
| Switzerland 01 | https://admin.ch-01.luware.cloud/ |
|---|---|
| Switzerland 02 | https://admin.ch-02.luware.cloud/ |
| Germany 01 | https://admin.dewe-01.luware.cloud/ |
| Germany 02 | https://admin.dewe-02.luware.cloud/ |
| United Kingdom 01 | https://admin.ukso-01.luware.cloud/ |
| Australia 01 | https://admin.aue-01.luware.cloud/ |
| West Europe 01 | https://admin.euwe-01.luware.cloud/ |
| East United States 01 | https://admin.use-01.luware.cloud/ |
✅ Make sure to configure your web proxies to allow access to these domains or whitelist the complete *.luware.cloud domain.
✅ Admin roles are granted by Luware Support or selected Service Partners. Details will be discussed during your Onboarding and first Nimbus Installation.
🔎The table below lists all detail permissions. In a nutshell, Admin user roles can do the following:
| Tenant Administrator |
|
|---|---|
| Organization Unit (OU) Administrator |
|
| Workflow (WF) Admin Limited |
|
Table: Nimbus Admin Portal Roles and Permissions
🔎Legend: Create, Read, Update, Delete, Execute.
Tenant
| Tab | Section | Property | Tenant Admin | OU Admin | WF Admin limited |
|---|---|---|---|---|---|
| General | - | Name | R | ||
| O365 Domain | R | ||||
| O365 Name | R | ||||
| Tenant Id | R | ||||
| Billing Address | RU | ||||
| Contact | - | Name | RU | ||
| RU | |||||
| Phone Number | RU | ||||
| SIP Address | RU | ||||
| Data Privacy | - | Allow Partner to see User Identifiers | RU | ||
| Allow Partner to see Customer Identifiers | RU | ||||
| Allow Partner to see Change History | RU | ||||
| Persist User States in Reporting | RU | ||||
| Data Retention Time (in Months) | R | ||||
| Show user Time in State | RU | ||||
| Enable Customer Overview | RU | ||||
| Allow to share Personal Identifiable Information (PII) | R | ||||
| Provisioning | - | Default OU for MS Teams creation | RU | ||
| Allow service provisioning via MS Teams | RU | ||||
| Enable Multihoming | R | ||||
| Default Team Owner Role | RU | ||||
| Enable Provisioning API | R | ||||
| Application Permissions | CRUD | ||||
| Extensions | Outbound | Directly Invite PSTN for Outbound Calls | R | ||
| Directly Invite UPN for Outbound Calls | R | ||||
| Max Scheduled Outbound Tasks per Service | R | ||||
| Interact | Interact enabled | RU | |||
| ACS connection string | RU | ||||
| O365 UserId | RU | ||||
| Widget Key | RE | ||||
| Session Recovery Timeout in Seconds | RU | ||||
| Authorization | RU | ||||
| Assistant | Use your own ACS instance | RU | |||
| Attendant Console | Global Contact Search MS Graph Filter | RU | |||
| Team Visibility | RU | ||||
| Presence Tracking | Grant Permission | E | |||
| Test UPN (secondary) | RU | ||||
| Modalities | Audio / Video | Leave Nimbus on Blind transfer | RU | ||
| Instant Messaging | Interact - Active | RU | |||
| Interact - Max concurrent IM Tasks per service | R | ||||
| Interact - Grant Permission | E | ||||
| Interact - Use your own account | RU | ||||
| Interact - Primary Account | RU | ||||
| Interact - Password (primary) | RU | ||||
| Interact - Test UPN (primary) | RU | ||||
| Interact - Secondary Account | RU | ||||
| Interact - Password (secondary) | RU | ||||
| Interact - Test UPN (secondary) | RU | ||||
| Interact - Use your own ACS instance | RU | ||||
| Interact - ACS connection string | RU | ||||
| Interact - ACS resource ID | RU | ||||
| Twilio - Active | RU | ||||
| Twilio - WhatsApp | RU | ||||
| Email Tasks | Max concurrent Email Tasks per Service | R | |||
| Licenses | - | Tenant State | R | ||
| Service | Advanced | R | |||
| Enterprise | R | ||||
| Contact Center Service | R | ||||
| Interact | R | ||||
| User | Attendant Console | R | |||
| Contact Center User | R | ||||
| Interact User | R | ||||
| Assistant | R | ||||
| Companion | R | ||||
| Modalities - Instant Message Modality | R | ||||
| Modalities - External Task Modality | R | ||||
| Modalities - Email Modality | R | ||||
| Virtual User | R |
Services
| Tab | Section | Property | Tenant Admin | OU Admin | WF Admin Limited |
|---|---|---|---|---|---|
| Grid1 | UI / View Access | Services | CRUD | CRUD | RU |
| Tasks | E | E | |||
| Download PowerShell Script | E | E | E | ||
| Tasks | Tasks List | RD | RD | ||
| Download Traces | E | E | |||
| Copy Trace Link | |||||
| Settings | General | Name | RU | RU | R |
| Service Display Name | RU | RU | R | ||
| Service UPN | RU | RU | R | ||
| Application ID | R | R | R | ||
| Organization Unit | RU | RU | R | ||
| PSTN Active | RU | RU | R | ||
| PSTN E.164 Number | RU | RU | R | ||
| Primary Opening Hours | RU | RU | R | ||
| Secondary Opening Hours | RU | RU | R | ||
| SLA Hangup | RU | RU | R | ||
| SLA Acceptance | RU | RU | R | ||
| Short Abandons Threshold in Seconds | RU | RU | R | ||
| Hide User Statistics from Reporting | RU | RU | R | ||
| Show on Historical Session Page | RU | RU | R | ||
| Licenses | RU | R | R | ||
| Addons | RU | R | R | ||
| Modalities | Audio Video checkbox | RU | RU | R | |
| Instant Messaging checkbox | RU | RU | R | ||
| External Task checkbox | RU | RU | R | ||
| Email checkbox | RU | RU | R | ||
| Audio Video - Inbound Conversations toggle | RU | RU | R | ||
| Audio Video - Audio Video Workflow dropdown (inbound) | RU | RU | R | ||
| Audio Video - Voice Message Channel | RU | RU | R | ||
| Audio Video - Outbound Conversations toggle | RU | RU | R | ||
| Audio Video - Outbound with Workflow toggle | RU | RU | R | ||
| Audio Video - Audio Video Workflow dropdown (outbound) | RU | RU | R | ||
| Instant Messaging - Interact toggle | RU | RU | R | ||
| Instant Messaging - Instant Messaging Workflow dropdown | RU | RU | R | ||
| Instant Messaging - Service System Messages | RU | RU | R | ||
| Instant Messaging - WhatsApp toggle | RU | RU | R | ||
| Instant Messaging - WhatsApp - Instant Messaging Workflow dropdown | RU | RU | R | ||
| Instant Messaging - WhatsApp - Messaging Entry | RU | RU | R | ||
| External Task - External Task Workflow dropdown | RU | RU | R | ||
| Email - Email Workflow dropdown | RU | RU | R | ||
| Email - Mailbox dropdown | RU | RU | R | ||
| Distribution | User Assignment Type | RU | RU | R | |
| Distribution Policy | RU | RU | R | ||
| Users Immediately Active | RU | RU | R | ||
| Conversation Distribution - Available | R | RU | R | ||
| Conversation Distribution - Dnd | R | RU | R | ||
| Conversation Distribution - Offline | R | RU | R | ||
| Conversation Distribution - Busy | RU | RU | R | ||
| Conversation Distribution - Away | RU | RU | R | ||
| Task Priority | RU | RU | R | ||
| ACW | RU | RU | R | ||
| Persistent RONA | RU | RU | R | ||
| Auto Redirect in Emergency Case | RU | RU | R | ||
| Redirect Destination | RU | RU | R | ||
| Extensions | Codes - Primary Codes | RU | RU | R | |
| Codes - Secondary Codes | RU | RU | R | ||
| Assistant - Assistant Conversation Context | RU | RU | R | ||
| Assistant - Service Call Templates | RU | RU | R | ||
| Attendant Console - Conversation Context | RU | RU | R | ||
| My Sessions - Conversation Context | RU | RU | R | ||
| My Sessions - Store Conversation Context Data toggle | RU | RU | R | ||
| My Sessions - Keep Context On Transfer - To Service | R | R | R | ||
| My Sessions - Keep Context On Transfer - To User | RU | RU | R | ||
| My Sessions - Widgets - Codes & Tags toggle | RU | RU | R | ||
| My Sessions - Widgets - Embedded Context toggle | RU | RU | R | ||
| My Sessions - Widgets - Embedded Context dropdown | RU | RU | R | ||
| My Sessions - Widgets - Live Caption toggle | RU | RU | R | ||
| My Sessions - Widgets - Transcript toggle | RU | RU | R | ||
| My Sessions - Widgets - Session Details toggle | RU | RU | R | ||
| My Sessions - Widgets - Map toggle | RU | RU | R | ||
| My Sessions - Widgets - Session Parameters | RU | RU | R | ||
| Permissions | Service Agents List | RU | RU | R | |
| Service Agents Levels and Profiles | |||||
| Service Owners List | RU | RU | R | ||
| Service Owners Levels and Profiles | |||||
| Users | Default Team Owner Role | RU | RU | R | |
| Team member can change active state | RU | RU | RU | ||
| Users - list | R | R | R | ||
| Users - Role - Member | R | R | R | ||
| Users - Role - Owner / Limited Team Owner | RU | RU | R | ||
| Users - Active toggle | RU | RU | RU | ||
| Interact | Interact - Active Toggle (general) | RU | RU | R | |
| Interact - Allowed Modalities - Audio&Video Toggle | RU | RU | R | ||
| Interact - Allowed Modalities - Instant Message Toggle | RU | RU | R | ||
| Interact - Restriction - Restrict Access Toggle | RU | RU | R | ||
| Interact - Restriction - Domain Templates Dropdown | RU | RU | R | ||
| Interact - Integration | RU | RU | R | ||
| Companion | Companion Tab | RU | RU | R | |
| Speech Recognizer | RU | RU | R | ||
| Transcription - Active toggle | RU | RU | R | ||
| Transcription - My Sessions toggle | RU | RU | R | ||
| Summarization - Active toggle | RU | RU | R | ||
| Summarization - My Sessions toggle | RU | RU | R | ||
| Summarized Items - Title | RU | RU | R | ||
| Summarized Items - Issue | RU | RU | R | ||
| Summarized Items - Recap | RU | RU | R | ||
| Summarized Items - Resolution | RU | RU | R | ||
| Summarized Items - Narrative | RU | RU | R | ||
| Virtual Assistants - Live Captioning toggle | RU | RU | R |
Users
| Tab | Section | Property | Tenant Admin | OU Admin | WF Admin Limited |
|---|---|---|---|---|---|
| Users | List / View | Users | CRUD | CRUD | |
| General | Display Name | R | R | ||
| Organization Unit | RU | RU | |||
| First Name | R | R | |||
| Last Name | R | R | |||
| UPN | R | R | |||
| O365 ID | R | R | |||
| Licenses | RU | RU | |||
| Modalities | RU | RU | |||
| Task Parallelization - Active | RU | RU | |||
| Services | Services (user belongs to) | R | R | ||
| Roles | Teams-based roles | R | R | ||
| Not Teams-based roles | RU | RU | |||
| Skills | Skills and levels | RU | RU | ||
| Profiles | Profiles | RU | RU | ||
| N/A Reasons | Not Available Reasons toggle | RU | RU | ||
| Not Available Reasons | RU | RU | |||
| Interact | User active | RU | RU | ||
| Audio & Video | RU | RU | |||
| Instant Message | RU | RU | |||
| Direct Message | RU | RU | |||
| Restrict Access | R | R | |||
| Domain Template | R | R | |||
| Integration | R | R | |||
| Assistant | Direct Call Templates | RU | RU |
Licensing
| Tab | Section | Property | Tenant Admin | OU Admin | WF Admin Limited |
|---|---|---|---|---|---|
| Licensing | - | Tenants Widget | |||
| Tenant State Widget | R | ||||
| Service Licenses Widget | R | ||||
| User Licenses Widget | R | ||||
| Level 1 (Tenants List) | |||||
| Level 2 (Licenses List) | R | ||||
| Edit licences icon | E | ||||
| Level 3 (Edit Popup) | RU |
Configuration
| Group | Section | Property | Tenant Admin | OU Admin | WF Admin Limited |
|---|---|---|---|---|---|
| Tenant | Organization Units | Organization Units | CRUD | ||
| Name | RU | ||||
| Parent | R | ||||
| Description | RU | ||||
| Workflows | Resources | Resources | CRUD | CRUD | CRUD |
| Name | RU | RU | RU | ||
| Organization Unit | RU | RU | RU | ||
| Audio File | RU | RU | RU | ||
| Playlists | Playlists | CRUD | CRUD | CRUD | |
| Name | RU | RU | RU | ||
| Organization Unit | RU | RU | RU | ||
| Playlist Entries | RU | RU | RU | ||
| Workflows | Workflow Instances | CRUD | CRUD | RU | |
| Name | RU | RU | R | ||
| Organization Unit | RU | RU | R | ||
| Template Type | R | R | R | ||
| Workflow Template | R | R | R | ||
| Workflow (Editor) | RU | RU | RU | ||
| Workflow Templates | Workflow Templates | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Template Type | R | R | |||
| Workflow Template (Selection) | R | R | |||
| Workflow Template (Editor) | RU | RU | |||
| Codes | Primary Codes | Primary Codes | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Description | RU | RU | |||
| Secondary Codes | Secondary Codes | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Description | RU | RU | |||
| User | Not Available Reasons | Not Available Reasons | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Custom Roles | Custom Roles grid | CRUD | |||
| Name | RU | ||||
| Organization Unit | RU | ||||
| Description | RU | ||||
| Administration Permissions (Tree) | RU | ||||
| Service | Conversation Context | Conversation Context | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| URL | RU | RU | |||
| Mailboxes | Name | CRUD | CRUD | ||
| Organization Unit | RU | RU | |||
| Email Address | RU | RU | |||
| Parameters | Parameters | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Default Value | RU | RU | |||
| ID | R | RU | |||
| Opening Hours | Opening Hours | CRUD | CRUD | RU | |
| Name | RU | RU | R | ||
| Organization Unit | RU | RU | R | ||
| Default | RU | RU | R | ||
| Periods | CRUD | CRUD | CRUD | ||
| AI | Speech Recognizers | Bots | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Type | RU | RU | |||
| Authentication Type | RU | RU | |||
| API Key | RU | RU | |||
| Endpoint | RU | RU | |||
| Speech Recognizer | Speech Recognizer | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Type | RU | RU | |||
| Region (MSFT) | RU | RU | |||
| Key | RU | RU | |||
| Multilanguage Toggle | RU | RU | |||
| Language (MSFT) | RU | RU | |||
| Bot Response Template | Bod Response Templates | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Description | RU | RU | |||
| Answer Formatted | RU | RU | |||
| Answer Raw | RU | RU | |||
| Exit | RU | RU | |||
| Custom Field Mapping | RU | RU | |||
| RU | RU | ||||
| Virtual Users | Virtual Users | RU | RU | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Description | RU | RU | |||
| Bot | RU | RU | |||
| Initial Message to Bot | RU | RU | |||
| Bot Response Template | RU | RU | |||
| Modalities - Audio Video | RU | RU | |||
| Modalities - Instant Messaging | R | R | |||
| Modalities - Email | R | R | |||
| Speech Recognizer | RU | RU | |||
| Licenses - Virtual User | RU | RU | |||
| Distribution | Skills | Skills | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Skill Categories | R | ||||
| Skill Categories | Skill Categories | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Skill Levels | RU | RU | |||
| Responsibility Levels | RU | RU | |||
| Distribution Policies | Distribution Policies | CRUD | CRUD | ||
| Name | RU | CRUD | |||
| Organization Unit | RU | CRUD | |||
| Order | RU | RU | |||
| Preferred User Routing | RU | RU | |||
| Waiting Time toggle | RU | RU | |||
| Waiting Time editbox | RU | RU | |||
| Last User Routing toggle | RU | RU | |||
| Last User Routing Treshold editbox | RU | RU | |||
| Distribution Levels | RU | RU | |||
| Responsibility Profiles | Responsibility Profiles | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Duty toggle | R | R | |||
| Instant Messaging | Direct System Messages | Direct System Messages grid1 | CRUD | CRUD | |
| General - Name | RU | RU | |||
| General - Organization Unit | RU | RU | |||
| General - Description | RU | RU | |||
| General - User | RU | RU | |||
| General - Custom Usert Display Name | RU | RU | |||
| Messages to User - "Acccept" Adaptive Card | RU | RU | |||
| Messages to User - "Terminate" Adaptive Card | RU | RU | |||
| Messages to User - Session Embed | RU | RU | |||
| Messages to Customer - Session Connected | RU | RU | |||
| Messages to Customer - Session Ended by User | RU | RU | |||
| Messages to Customer - Session Declined by User | RU | RU | |||
| Service System Messages | Service System Messages grid1 | CRUD | CRUD | ||
| General - Name | RU | RU | |||
| General - Organization Unit | RU | RU | |||
| General - Description | RU | RU | |||
| General - User | RU | RU | |||
| General - Custom User Display Name | RU | RU | |||
| General - Custom User Display Name | RU | RU | |||
| Messages to User - "Acccept" Adaptive Card | RU | RU | |||
| Messages to User - "Terminate" Adaptive Card | RU | RU | |||
| Messages to User - Session Embed | RU | RU | |||
| Messages to Customer - Session Connected | RU | RU | |||
| Messages to Customer - Session Ended by User | RU | RU | |||
| Provider Connectors | Provider Connector grid | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Type | RU | RU | |||
| API Key SID | RU | RU | |||
| API Key Secret | RU | RU | |||
| Region | RU | RU | |||
| Messaging Entries | Conversation Services grid | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Provider Connector | RU | RU | |||
| Service SID | RU | RU | |||
| Attendant Console | Address Books | Address Books | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | CRUD | |||
| Image | RU | CRUD | |||
| Interact | Domain Templates (CORS) | Domain Templates (CORS) | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Domain | RU | RU | |||
| Nimbus Assistant | Direct Call Templates | Direct Call Templates | CRUD | CRUD | |
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Description | RU | RU | |||
| Trigger Event | RU | RU | |||
| Call Type | R | R | |||
| Actions | RU | RU | |||
| Inbound Internal Teams Calls | RU | RU | |||
| Inbound PSTN Calls | RU | RU | |||
| Inbound External Teams Calls | RU | RU | |||
| Service Call Templates | Service Call Templates | CRUD | CRUD | ||
| Name | RU | RU | |||
| Organization Unit | RU | RU | |||
| Description | RU | RU | |||
| Trigger Event | RU | RU | |||
| Call Type | R | R | |||
| Actions | RU | RU | |||
| Inbound Internal Teams Calls | RU | RU | |||
| Inbound External Teams Calls | RU | RU | |||
| Inbound PSTN Calls | RU | RU | |||
| Outbound Service Calls | RU | RU | |||
| External Task | RU | RU | |||
| Instant Messaging | RU | RU | |||
| RU | RU |
Operations
| Tab | Section | Property | Tenant Admin | OU Admin | WF Admin Limited |
|---|---|---|---|---|---|
| Service | Widgets | Tenant dropdown | R | ||
| Service dropdown | RU | ||||
| Tasks doughnut | R | ||||
| Tasks list | RD | ||||
| Last Interaction | R | ||||
| Interactions | R | ||||
| Last Updated | RE | ||||
| History | R | ||||
| Download Traces | E | ||||
| Copy Trace Link | |||||
| Customer | Widgets | Tenant dropdown | R | ||
| Customer dropdown | RU | ||||
| Last Interaction | R | ||||
| Interactions | R | ||||
| History | R | ||||
| Download Traces | E | ||||
| Copy Trace Link | |||||
| Change History | Widgets | Tenant dropdown | RU | ||
| Last Updated | RE | ||||
| Change History | R | ||||
| Details view | R | ||||
| Task Management | Widgets | Tenant Dropdown | |||
| Task List & Remove Tasks | RD |
1 The term “grid” describes a permission to list (and potentially manipulate) already existing entries of the same type.
User Portal Permissions
Portal Roles
NOTES
Roles described on this page have access to the Nimbus (Frontend) Portal.
Show Portal URLs…
Nimbus Portal URLs
| Switzerland 01 | https://portal.ch-01.luware.cloud/ |
|---|---|
| Switzerland 02 | https://portal.ch-02.luware.cloud/ |
| Germany 01 | https://portal.dewe-01.luware.cloud/ |
| Germany 02 | https://portal.dewe-02.luware.cloud/ |
| United Kingdom 01 | https://portal.ukso-01.luware.cloud/ |
| Australia 01 | https://portal.aue-01.luware.cloud/ |
| West Europe 01 | https://portal.euwe-01.luware.cloud/ |
| East United States 01 | https://portal.use-01.luware.cloud/ |
✅ Make sure to configure your web proxies to allow access to these domains or whitelist the complete *.luware.cloud domain.
✅ Portal Roles are granted depending on Service type, as Services can be provisioned with different User Assignment Types:
Learn more about User Assignment…
INC User Assignment Types
Each Nimbus Service can be of a different User Assignment Type that determines how Users are associated to this Service:
- MS Teams-based: Directly tied to the Team itself in MS Teams, determined during Service Provisioning. Users get automatically added and synced to a Nimbus Service.
- Skill-based: Applies for manually created Services via Nimbus Service Administration. Requires skill-assignment to Users you manually assign to the Service from within your Tenant directory.
- None: Primarily used for IVR or first-level redirection Services. This Service has no Users and is therefore primarily configured by any Administrator.
☝ Important to know: The User Assignment Type setting is fixated when a Service was either provisioned via MS Teams or manually created via Service Administration, e.g. either for Customer IVR or User skill-based task distribution purposes. A switch between MS Teams-based and Skill-based Services is not possible due to how individual Users are configured and how related Nimbus Features operate.
🔎The table below lists all detail permissions. In a nutshell, Portal user roles can do the following:
| Tenant Administrator |
|
|---|---|
| Organization Unit (OU) Administrator |
|
| Workflow (WF) Admin Limited |
|
| User Supervisor(1) |
Contact Center Requires a Contact Center license on the user. An addition to an Owner-type role, manually granted via User Administration.
|
| Service Supervisor(1) |
Contact Center Requires a Contact Center license on the user. An addition to an Owner-type role, manually granted via User Administration.
|
| Contact Center (CC) User |
Contact Center Requires a Contact Center (CC) license on the General User Settings.
|
| Service Owner |
Contact Center Requires a Contact Center (CC) license on the General User Settings.
|
| Service Agent |
Contact Center Requires a Contact Center (CC) license on the General User Settings. An associated Microsoft Teams channel is not required anymore, so the user can act as “standalone” specialist for dedicated tasks.
|
| Team Owner |
Default role granted during Service Provisioning via MS Teams.
|
| Team Owner Limited |
A reduced role that can be granted during Service Provisioning via MS Teams.
|
| Team Member |
A Nimbus user synched from the Tenant's user directory.
|
(1) GDPR General Data Access limitation: If a user has a Supervisor but not a Team Owner / Service Admin role within a service, only limited datasets in the historical BI Template will be shown. Other tabs and queries in the Power BI Report may appear blank.
☝ This is intended by design. To see a full dataset (including live Reporting data on the portal), the same user also needs a "Service/Team Owner" role assigned for the respective service(s).
(2) Nimbus “Team” roles are only referenced to limit access to Nimbus-related functionality. Vice-versa, MS Teams roles are not affected by Nimbus role assignment. Even in a “limited” Nimbus role - Team Owners can continue to act with all their non-Nimbus related privileges within MS Teams.
(3) ☝Data visibility consideration: Note that MS Teams “Guests” may also get “indirect” access to Nimbus service data, e.g. by seeing call context posted in Adaptive Cards in generally available chat channels. → We recommend to review your MS Teams user privileges regularly to prevent data leaks.
Table: Nimbus Frontend Portal Roles and Permissions
🔎Legend: Create, Read, Update, Delete, Execute.
My Services
| Section | Service Supervisor | CC User | Team Member | Service Agent | Team / Service Owner | Team Owner Limited |
|---|---|---|---|---|---|---|
| My Services | R | R | R | R | R | |
| Service Settings icon | E | E | E | |||
| Call On Behalf | E | E | E | E | ||
| Users - Own Active Toggle | N/A | RU | N/A | RU | RU | |
| Users - Active Toggle | R | N/A | R | N/A | RU | RU |
| Users - Presence icon | R | R | R | R | R | |
| Pickup | N/A | E | N/A | E | E |
Customer Overview
| Tab | Section | Service Supervisor | CC User | Team Member | Service Agent | Team / Service Owner | Team Owner Limited | |
|---|---|---|---|---|---|---|---|---|
| Customer Overview | Customer Insights | Basic Access | R | R | R | |||
| Extended Access (User Sessions) | R | R | ||||||
Service Details
| Tab | Section | OU Admin | WF Admin Limited | Service Supervisor | CC User | Team Member | Service Agent | Team / Service Owner | Team Owner Limited | |
|---|---|---|---|---|---|---|---|---|---|---|
| Dashboard | Dashboard | R | R | R | R | R | ||||
| Users List | R | R | R | R | R | |||||
| Users - Own Active Toggle | N/A | N/A | RU | N/A | RU | RU | ||||
| Users - Active Toggle | RU | N/A | R | N/A | RU | RU | ||||
| Pickup | N/A | E | N/A | E | E | |||||
| Today's Reporting KPIs | R | R | R | R | R | |||||
| Reporting | Service Statistics | R | R | R | R | R | ||||
| Tasks Heatmap | R | R | R | R | R | |||||
| Users Statistics | R | R | R | R | R | |||||
| Historical Sessions | Session Results | R | R | R | ||||||
| Sessions | R | R | R | |||||||
| Session Types | R | R | R | |||||||
| Session Directions | R | R | R | |||||||
| Historical Sessions - Service Sessions | R | R | R | |||||||
| Historical Sessions - User Sessions | R | R | R | |||||||
| Session Details Popup | R | R | R | |||||||
| Settings | General | Name | RU | R | R | RU | R | |||
| Service Display Name | RU | R | R | RU | R | |||||
| Service UPN | RU | R | R | RU | R | |||||
| Application ID | R | R | R | R | R | |||||
| Organization Unit | RU | R | R | RU | R | |||||
| PSTN Active | RU | R | R | RU | R | |||||
| PSTN E.164 Number | RU | R | R | RU | R | |||||
| Primary Opening Hours | RU | R | RU | RU | RU | |||||
| Secondary Opening Hours | RU | R | RU | RU | RU | |||||
| SLA Hangup | RU | R | RU | RU | RU | |||||
| SLA Acceptance | RU | R | RU | RU | RU | |||||
| Short Abandons Threshold in Seconds | RU | R | RU | RU | RU | |||||
| Show on Historical Session Page | RU | R | R | R | R | |||||
| Hide User Statistics from Reporting | RU | R | R | R | R | |||||
| Show on Historical Sessions Page | RU | R | R | R | R | |||||
| Modalities | Audio Video checkbox | RU | R | R | RU | R | ||||
| Instant Messaging checkbox | RU | R | R | RU | R | |||||
| External Task checkbox | RU | R | R | RU | R | |||||
| Email checkbox | RU | R | R | RU | R | |||||
| Audio Video - Inbound Conversations toggle | RU | R | R | RU | R | |||||
| Audio Video - Audio Video Workflow dropdown (inbound) | RU | R | R | RU | R | |||||
| Audio Video - Voice Message Channel | RU | R | R | RU | R | |||||
| Audio Video - Outbound Conversations toggle | RU | R | R | RU | R | |||||
| Audio Video - Outbound with Workflow toggle | RU | R | R | RU | R | |||||
| Audio Video Workflow dropdown (outbound) | RU | R | R | RU | R | |||||
| Instant Messaging - Interact toggle | RU | R | R | RU | R | |||||
| Instant Messaging - Instant Messaging Workflow dropdown | RU | R | R | RU | R | |||||
| Instant Messaging - Service System Messages | RU | R | R | RU | R | |||||
| Instant Messaging - WhatsApp toggle | RU | R | R | RU | R | |||||
| Instant Messaging - WhatsApp - Instant Messaging Workflow dropdown | RU | R | R | RU | R | |||||
| Instant Messaging - WhatsApp - Messaging Entry | RU | R | R | RU | R | |||||
| External Task - External Task Workflow dropdown | RU | R | R | RU | R | |||||
| Email - Email Workflow dropdown | RU | R | R | RU | R | |||||
| Email - Mailbox dropdown | RU | R | R | RU | R | |||||
| Distribution | User Assignment Type | RU | R | R | RU | R | ||||
| Distribution Policy | RU | R | R | RU | R | |||||
| Users Immediately Active | RU | R | R | RU | R | |||||
| Conversation Distribution - Available | R | R | R | R | R | |||||
| Conversation Distribution - Dnd | R | R | R | R | R | |||||
| Conversation Distribution - Offline | R | R | R | R | R | |||||
| Conversation Distribution - Busy | RU | R | R | RU | R | |||||
| Conversation Distribution - Away | RU | R | R | RU | R | |||||
| Task Priority | RU | R | R | RU | R | |||||
| ACW | RU | R | R | RU | R | |||||
| Auto Redirect in Emergency Case | RU | R | R | R | R | |||||
| Redirect Destination | RU | R | R | R | R | |||||
| RONA | RU | R | R | RU | R | |||||
| Extensions | Codes - Primary Codes | RU | R | R | RU | R | ||||
| Codes - Secondary Codes | RU | R | R | RU | R | |||||
| Assistant - Assistant Conversation Context | RU | R | R | RU | R | |||||
| Assistant - Service Call Templates | RU | R | R | RU | R | |||||
| Attendant Console - Conversation Context | RU | R | R | RU | R | |||||
| My Sessions - Conversation Context | RU | R | R | RU | R | |||||
| My Sessions - Store Conversation Context Data toggle | RU | R | R | RU | R | |||||
| My Sessions - Keep Custom Context Parameters on transfer - To Service | RU | R | R | RU | R | |||||
| My Sessions - Keep Custom Context Parameters on transfer - To User | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Codes & Tags toggle | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Embedded Context toggle | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Embedded Context dropdown | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Live Caption toggle | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Transcript toggle | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Session Details toggle | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Map toggle | RU | R | R | RU | R | |||||
| My Sessions - Widgets - Session Parameters | RU | R | R | RU | R | |||||
| Agents | Service Agents List | R | R | R | R | R | ||||
| Service Agents Levels and Profiles | RU | RU | ||||||||
| Service Owners List | R | R | R | R | R | |||||
| Service Owners Levels and Profiles | RU | RU | ||||||||
| Users | Default Team Owner Role | RU | R | R | R | |||||
| Team member can change active state | RU | RU | RU | R | ||||||
| Users - list | R | R | R | R | ||||||
| Users - Role - Member | R | R | R | R | ||||||
| Users - Role - Owner / Limited Team Owner | RU | R | R | R | ||||||
| Active toggle | RU | RU | RU | RU | ||||||
| Companion | Speech Recognizer Dropdown | RU | R | R | RU | R | ||||
| Transcription Toggle | RU | R | R | RU | R | |||||
| Live Captioning Toggle | RU | R | R | RU | R | |||||
Configuration
| Tab | Section | OU Admin | WF Admin | Service Supervisor | Team / Service Owner | Team Owner Limited | |
|---|---|---|---|---|---|---|---|
| Workflows | Resources | Resources grid1 | CRUD | CRUD | CRUD | CRUD | |
| Name | RU | RU | RU | RU | |||
| Organization Unit | RU | RU | R | R | |||
| Audio File | RU | RU | RU | RU | |||
| Playlists | Play List grid1 | CRUD | CRUD | CRUD | CRUD | ||
| Name | RU | RU | RU | RU | |||
| Organization Unit | RU | RU | R | R | |||
| Play List | RU | RU | RU | RU | |||
| Workflows | Workflow grid1 | CRUD | RU | CRUD | CRUD | ||
| Name | RU | R | RU | RU | |||
| Organization Unit | RU | R | R | R | |||
| Template Type | R | R | R | R | |||
| Workflow Template | R | R | R | R | |||
| Workflow | RU | RU | RU | RU | |||
| Codes | Primary Codes | Primary Codes grid1 | CRUD | CRUD | |||
| Name | RU | RU | |||||
| Organization Unit | RU | R | |||||
| Description | RU | RU | |||||
| Secondary Codes | Secondary Codes grid1 | CRUD | CRUD | ||||
| Name | RU | RU | |||||
| Organization Unit | RU | R | |||||
| Description | RU | RU | |||||
| Service | Conversation Context | Conversation Context grid1 | CRUD | CRUD | |||
| Name | RU | RU | |||||
| Organization Unit | RU | R | |||||
| URL | RU | RU | |||||
| Parameters | Parameters grid1 | CRUD | CRUD | ||||
| Name | RU | RU | |||||
| Organization Unit | RU | R | |||||
| Default Value | RU | RU | |||||
| ID | RU | R | |||||
| Opening Hours | Opening Hours grid1 | CRUD | RU | CRUD | CRUD | CRUD | |
| Name | RU | R | RU | RU | RU | ||
| Organization Unit | RU | R | RU | R | R | ||
| Default | RU | R | RU | RU | RU | ||
| Periods | CRUD | CRUD | CRUD | CRUD | CRUD | ||
Flexible Dashboards
Contact Center - Non-Personal Dashboards and Personal Dashboards require a Contact Center license on the user to become accessible. Each Dashboard can be customized with Dashboard Widgets.
🔎 W = Widget access. A user needs a Contact Center license to see Dashboards, and can add Dashboard Widgets. However, seeing data (Services / Users / OUs) inside those widgets requires an additional R permission (e.g. Team Member, Agent role) within the service / team.
| Tab | Section | User Supervisor | Service Supervisor | CC User | Team Member | Service Agent | Team / Service Owner | Team Owner Limited | |
|---|---|---|---|---|---|---|---|---|---|
| Dashboards | Personal Dashboards | CRUD | |||||||
| Non-Personal Dashboards | R | ||||||||
| Dashboard Widgets | Service | Service KPI Tile | R | W | R | R | R | ||
| Service KPI Tabular | R | W | R | R | R | ||||
| Service KPI Chart | R | W | R | R | R | ||||
| Service KPI Comparison Chart | R | W | R | R | R | ||||
| Service KPI Graph | R | W | R | R | R | ||||
| Service Queue Tabular | R | W | R | R | R | ||||
| Live Service Tasks Tabular | R | W | R | R | R | ||||
| Service Outbound Tasks Tabular | RE | W | R | R | RE | ||||
| Service External Tasks Tabular | RE | W | R | R | RE | ||||
| Service Heatmap | R | W | R | R | R | ||||
| Service Supervision | WRE | W | |||||||
| User | User Performance Tabular | R | W | ||||||
| User State Tabular | R | W | R | ||||||
| User Supervisor Tabular | RE | W | |||||||
| User State Chart | R | W | R | ||||||
| User Tile | R | W | R | ||||||
| Common | Markdown | WR | |||||||
| Date & Time | WR | ||||||||
| Embedded Website | WR | ||||||||
1 Note: The term “grid” describes a permission to list (and potentially manipulate) already existing entries of the same type.
Power Automate User Permissions
Power Automate Roles
INC Power Automate Connector Change Notice
📆Upcoming change: New Power Automate connector user role validation
We're introducing an important enhancement to the Nimbus Power Automate Connector, rollout planned on 15th of January 2026. This update is designed to improve security and ensure that flows are only triggered by users with valid permissions.
☝What is changing:
- Currently, users must hold a Power Automate Role in Nimbus - either Service Owner or Administrator. The role is validated when creating a flow.
- With this upcoming update, an additional step will be introduced, validating roles at each execution of a flow. This effectively prevents flow-execution by users who no longer have the appropriate access.
✅Action required: We recommend for all our customers using the Power Automate Connector to review and confirm their flow configuration to avoid any disruption. Keep in mind that the new validation will not just check the role but also the Organization Unit scope under which the user operates. Any later changes in the user's OU scope will also affect existing flows - e.g. the services that the user can see and impact.
🔎Certified and Custom Connector differences
All Roles listed in the table below have access to the Nimbus Power Automate Connector, however with varying Execution rights. Note that your installed Legacy & Custom Connectors may still work using these roles, but will not receive access to new features, e.g. new Triggers and Actions.
✅Consider a Connector Migration to the certified connector as soon as possible and check the Flow-executing user role to ensure a smooth transition.
Table: Nimbus Power Automate Permissions
🔎Legend: Create, Read, Update, Delete, Execute
| Certified Connector | Custom Connector | Tenant Admin | OU Admin | Team/Service Owner | Team Owner Limited | ||
|---|---|---|---|---|---|---|---|
| Conversations | Triggers | - | GetOnNewTasks | E | E | ||
| When a task changes state | GetOnUpdatedTasks | E | E | ||||
| When the virtual task assistant has an update | E | E | |||||
| Actions | Update task | UpdateTask | E | E | |||
| Add a new external task | AddExternalTask | E | E | ||||
| Remove an external task | RemoveExternalTask | E | E | ||||
| Get Data from Virtual Task Assistant | E | E | |||||
| Address Books | Actions | Add a contact to an address book | AddOrUpdateContact | E | E | ||
| Update a contact in an address book | - | E | E | ||||
| Empty an address book | ClearContacts | E | E | ||||
| Get contact(s) from ana address book | GetContacts | E | E | ||||
| Remove contact(s) from an address book | RemoveContacts | E | E | ||||
| Outbound Service Calls | Triggers | When a scheduler entry changes state | GetOnUpdatedOutboundTask | E | E | ||
| Actions | Schedule a new outbound call | AddOrUpdateOutboundTask | E | E | |||
| Get all scheduler entries | GetOutboundTasks | E | E | ||||
| Update a scheduler entry | - | E | E | ||||
| Remove a scheduler entry | RemoveOutboundTask | E | E | ||||
Reporting User Permissions
Reporting Roles
NOTES
🔎Roles described in the table below have access to Historical Sessions summarized in a Nimbus Power BI Report Template.
✅ When Setting Up Power BI and connecting to the OData Feed (e.g. via the Report Template or other means), any of the user roles below are required. The Organization Unit of the connecting user account determines, which service and user data will become available in the data query.
🔎Legend: Create, Read, Update, Delete, Execute
| Historical Session & User Data(1) | Tenant Administrator | User Supervisor | Service Supervisor | Team / Service Owner | Team Owner Limited |
|---|---|---|---|---|---|
| Unified Sessions(2) | R | R | R | R | |
| Service Sessions(2) | R | R | R | R | |
| User Sessions(2) | R | R | R | R | |
| Transfer Sessions(2) | R | R | R | R | |
| User States | R | ||||
| Service Session Aggregates(3) | R | R | R | R | |
| User Session Aggregates(3) | R | R | R | R | |
| User State Aggregates(3) | R | ||||
| Direct Call Data | R | R |
(1) All data is built from the Nimbus Reporting Model.
(2) Refer to Nimbus Reporting for an overview of available Session Types.
(3) Refer to Data Aggregation.